You can set WebAPI2 access filters under the Security settings. You can set WebAPI2 access filter access filter on server level - you can not set them on user or domain specific security filters. With this filter you specify the rules for accessing webapi2 methods.
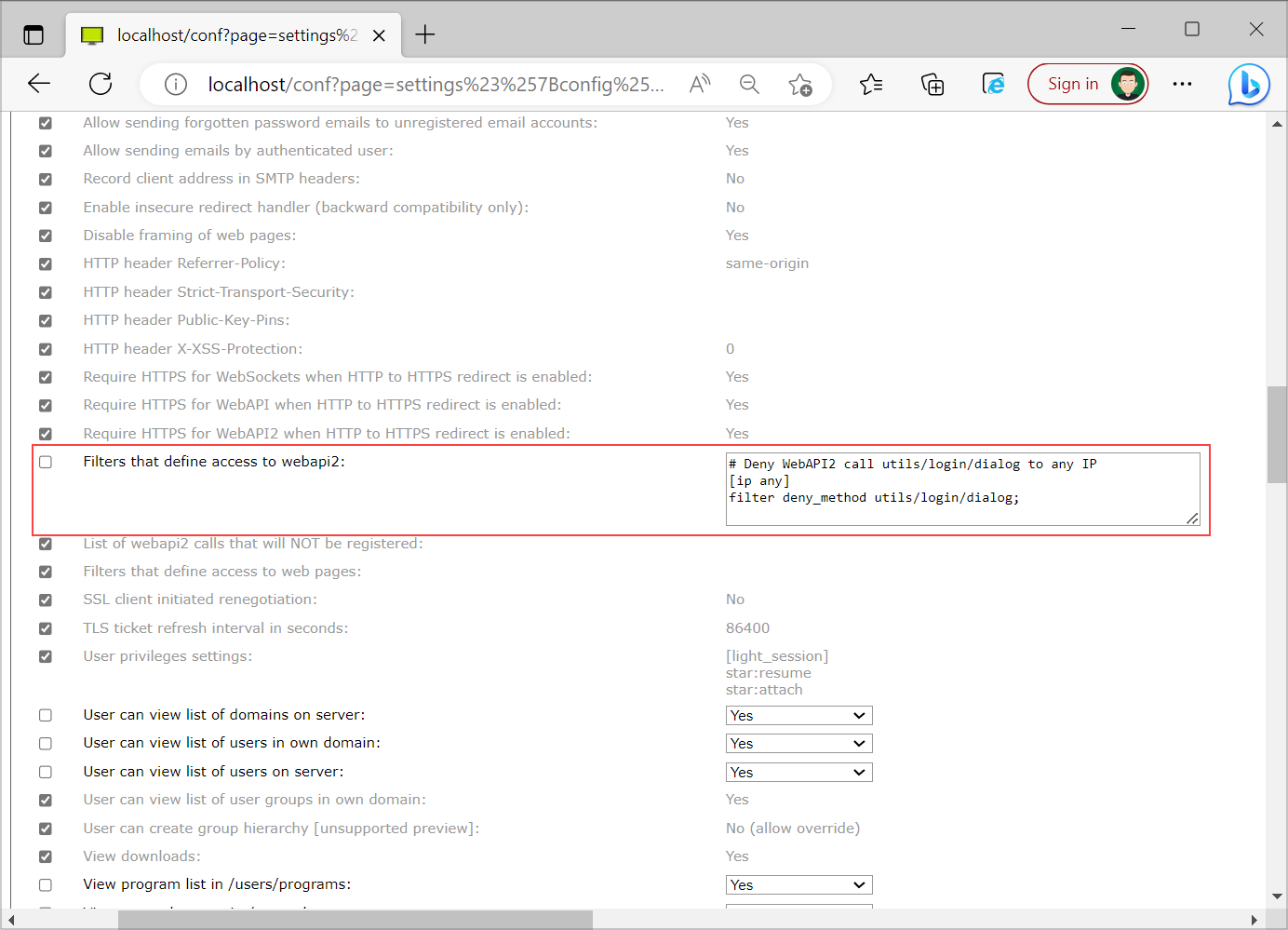
In the example above you can deny WebAPI2 method utils/login/dialog for any IP address. The setting will deny any version of utils/login/dialog/ method, because filter matches all versions (utils/login/dialog/*). Instead of ip any you can also use a specific IP address or an IP address range.
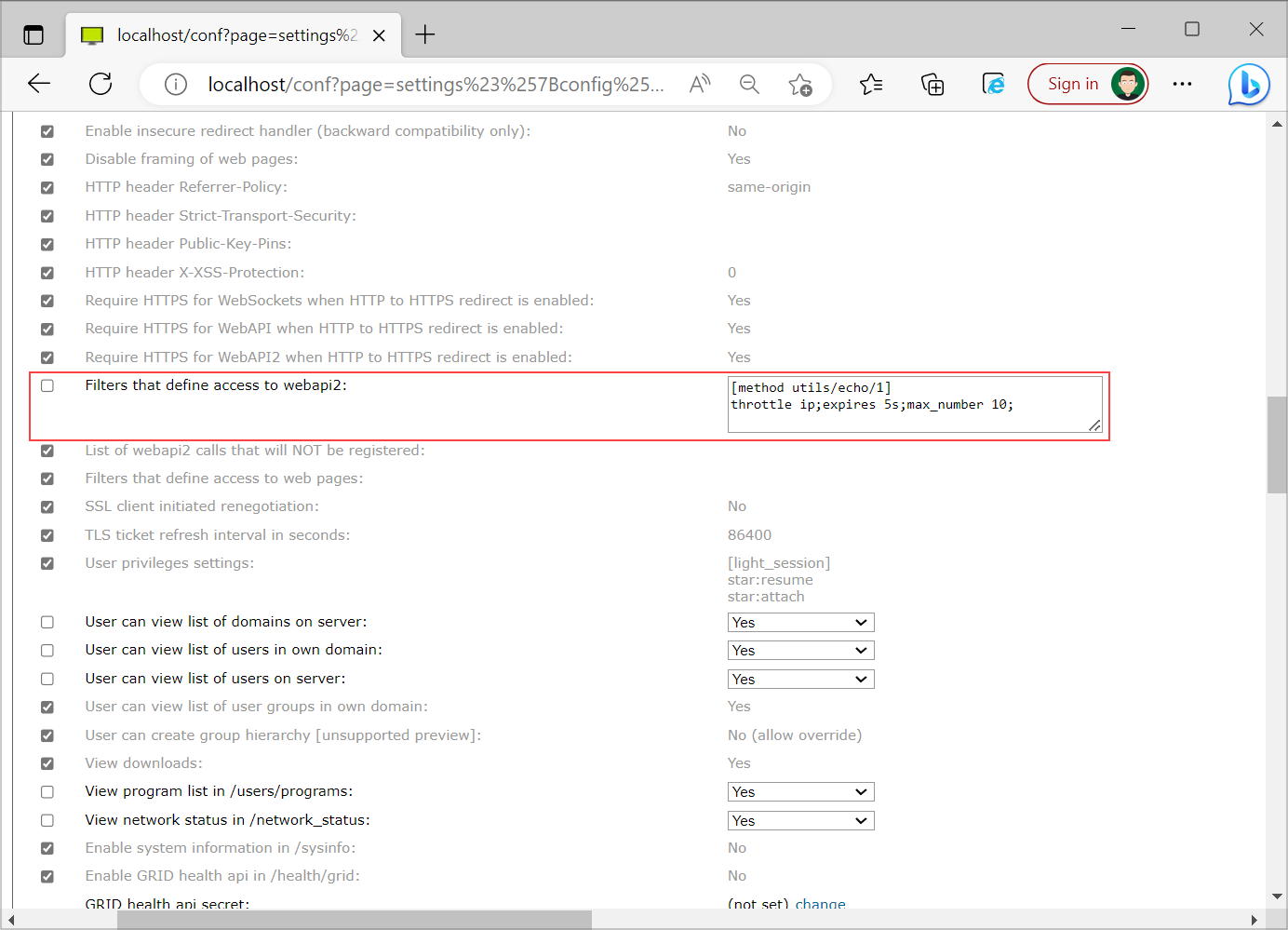
You can limit access to any WebAPI2 call for all users from one specific IP. From the example above, method utils/echo/1 can be called only 10 times in a 5 second range. You can set the expiration range in milliseconds (ms), seconds (s), minutes (m) or hours (h).
NOTE: When using throttle filter, every call has its own timer - in the example above, if you call method echo 5 times in the first second and 6 times in fourth second, last call will be denied (because the limit is 10). Every other call in the range of 5 seconds would be denied too. But you can repeat 3 calls in the sixth second, as the timer for the first 3 calls would already run out.
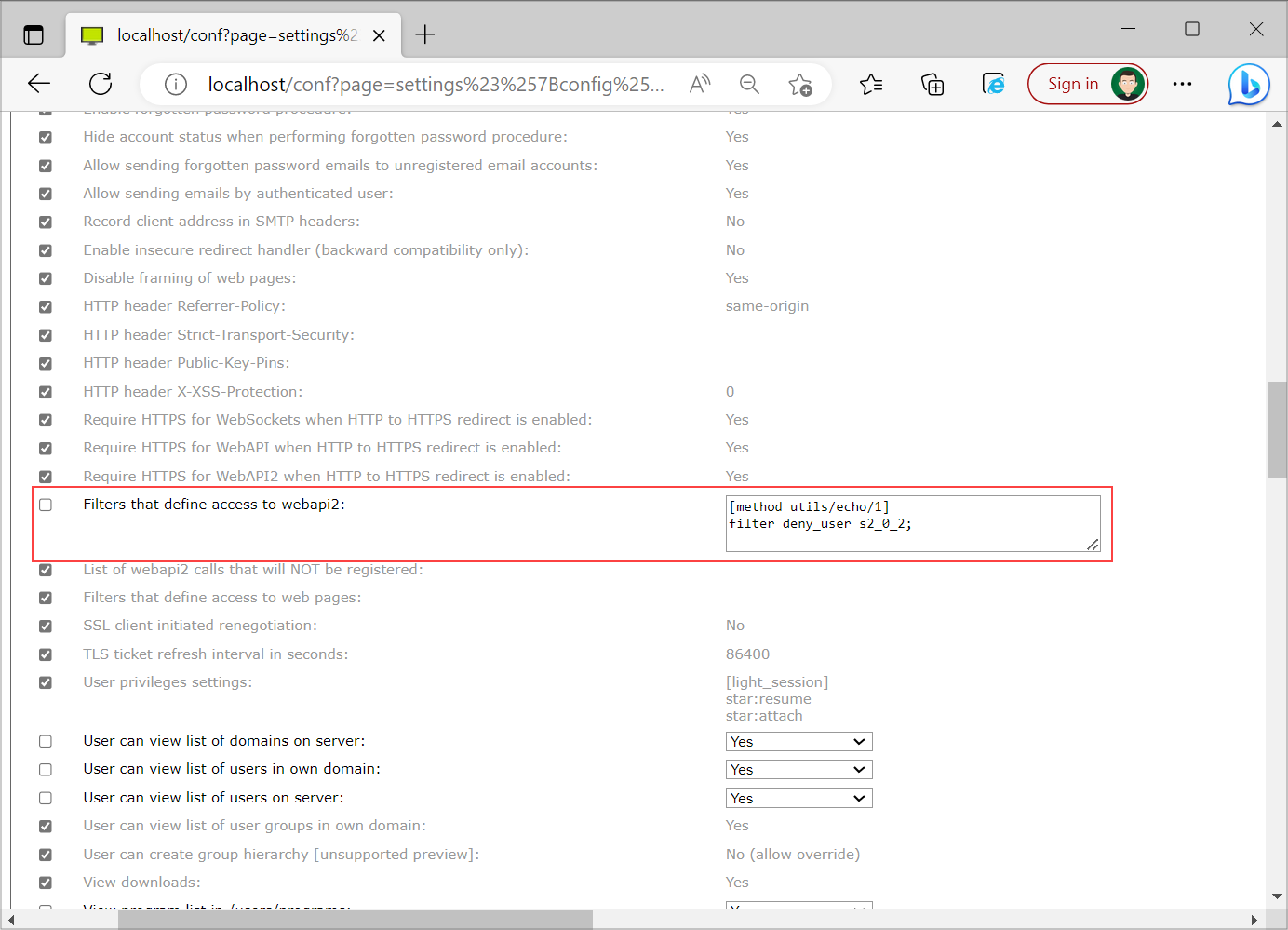
You can also deny a specific user from calling a specific method - in the example above you deny user with ID s2_0_2 from calling the method utils/echo/1.
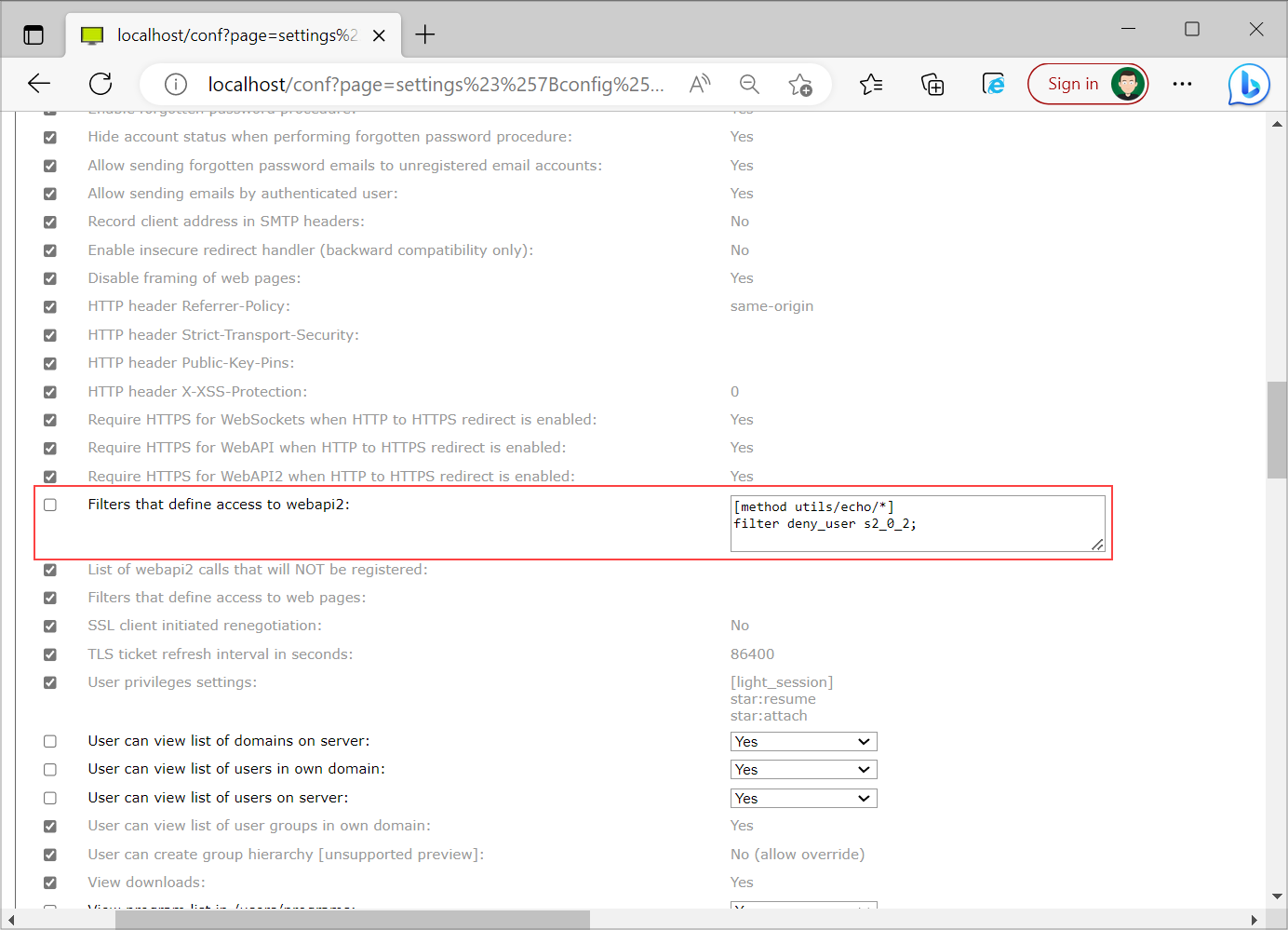
You don't need to use an exact method version, instead you can use a wildcard to match the method name with all existing versions - example above is the same as the previous example with version (utils/echo/1).
All possible combinations for webapi2 access filter are:
[ip any OR ip <specific ip> OR ip <ip range>] filter deny_method <method name>; filter deny_user <user ID>; throttle user;expires <range>s;max_number <maximum_attempts>; throttle method;expires <range>s;max_number <maximum_attempts>; [method <method name with method version> OR method <method name with wildcard>] filter deny_user <user ID>; throttle ip;expires <range>s;max_number <maximum_attempts>; throttle user;expires <range>s;max_number <maximum_attempts>;
A few examples for WebAPI2 Access Filter setting:
# Deny WebAPI2 calls utils/login/1 and utils/login/2 to all IPs [ip any] filter deny_method utils/login; # Deny WebAPI2 call utils/login/dialog/1 to a defined IP [ip 1.2.3.4] filter deny_method utils/login/dialog/1; # Deny WebAPI2 calls utils/login/1 and utils/login/2 to a subnet [ip 1.2.3.0/255.255.255.0] filter deny_method utils/login; # Deny all WebAPI2 calls to an user s1_0_3 from any IP [ip any] filter deny_user s1_0_3; # Throttle any user from any ip if he calls 10 WebAPI2 calls in 5 seconds [ip any] throttle user;expires 5s;max_number 10; # Throttle any method for any ip if the method is called 10 times in 5 seconds [ip any] throttle method; expires 5s;max_number 10; # Deny user with id s1_0_3 to a WebAPI2 call to search for remote computers [method islalwayson/computer/search/*] filter deny_user s1_0_3; # Throttle any ip if methods isllight/session/list/* are called 10 times in 5 seconds [method isllight/session/list/*] throttle ip;expires 5s;max number_10; # Throttle any user if methods isllight/session/list/* are called 10 times in 5 seconds [method isllight/session/list/*] throttle user;expires 5s;max number_10;
Here are some examples of what error message would an end user receive if the WebAPI2 for login is denied for them: