We are aware that the security of remote desktop is of utmost importance to you and your clients when using ISL Online remote computer software, therefore it is our top priority to assure you the highest level of remote desktop security. This security statement presents a detailed technical background of the ISL Online technology and reveals how secure is ISL Online's remote desktop. The provided information should help you understand several security layers implemented in the ISL Online products.
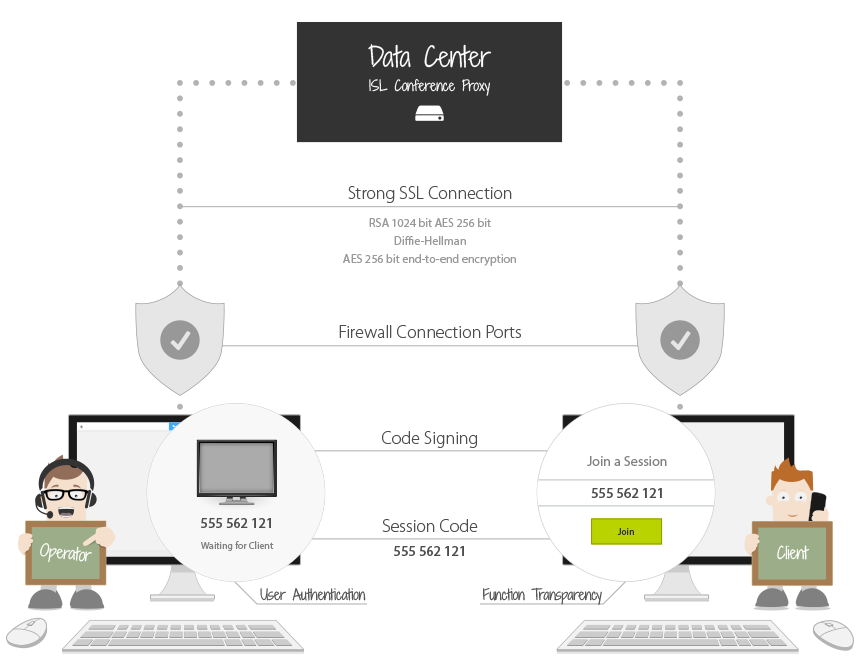
ISL Online' s remote desktop security in short: industry-standard (SSL) security technologies are used to protect data transfer; RSA 2048 Bit Public / Private Key Exchange (RSA 1024 bit for versions older than 4.4.1823.8 ) is used to negotiate symmetrical AES 256 Bit end-to-end encryption; end-user applications are digitally signed by means of a code signing certificate.
Note: Following the top security standards we added support for SHA-2 certificates. Code is now signed twice on our end, with SHA-1 and SHA-2 signature to enable backwards compatibility with older systems that support only SHA-1 and to provide the best possible security to systems that support SHA-2.
3-level encryption and maximum security:
Learn more about security policy: www.islonline.com/technology/security-statement.htm.